ICAM
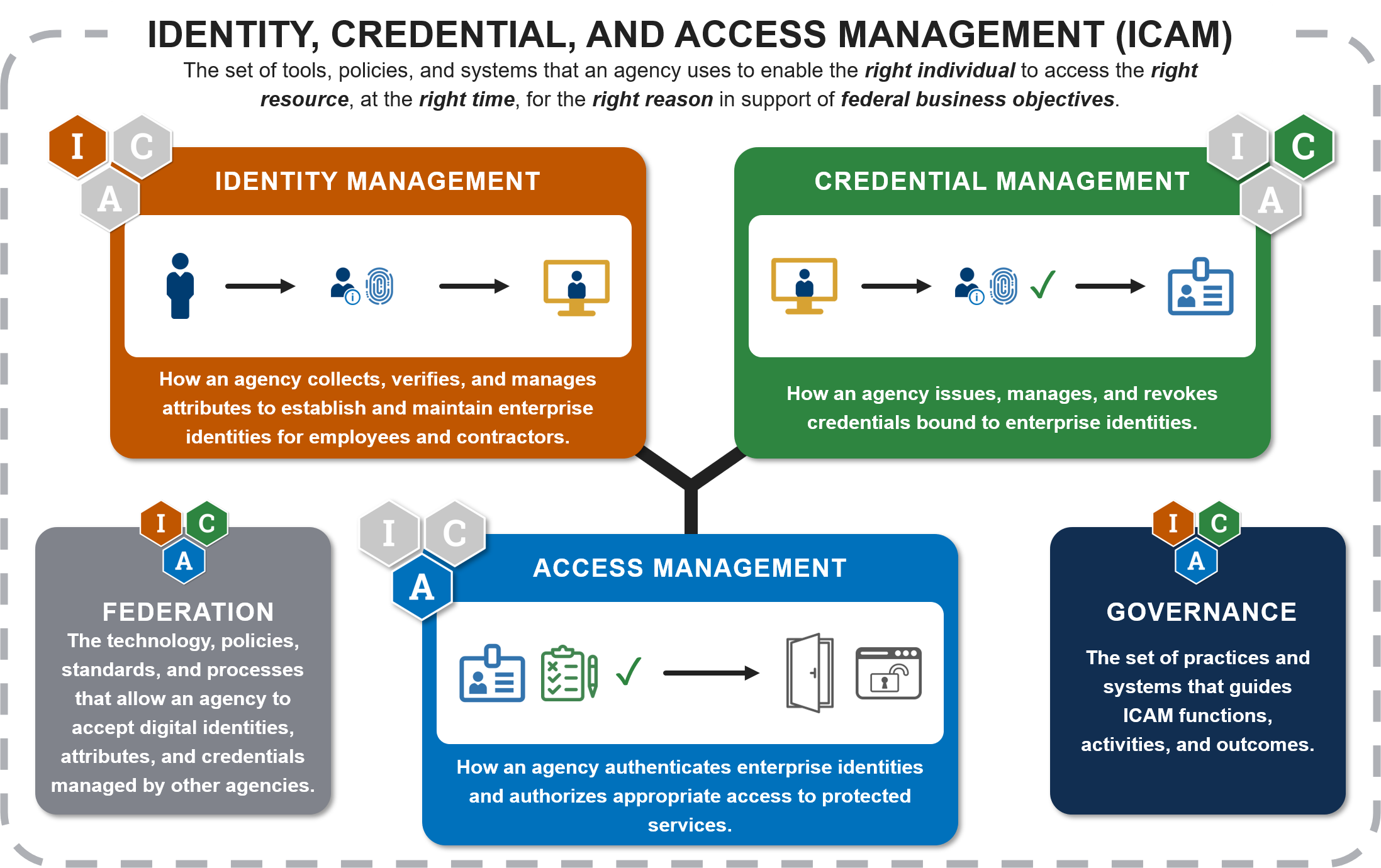
The following diagram offers a view of the ICAM practice areas and supporting elements.
Action: Copy the graphics and text to use at your agency to drive ICAM awareness, strategy development, and communications.
ICAM is the set of tools, policies, and systems that an agency uses to enable the right individual to access the right resource, at the right time, for the right reason in support of federal business objectives.
Agencies implement ICAM services and solutions to unify their IT services, strengthen physical access control, and improve information security. Understanding the ICAM building blocks is key to understanding the FICAM architecture.
ICAM consists of three practice areas and two supporting elements. The supporting elements enhance practice area capabilities.
| ICAM Practice Areas | |
 |
Identity Management is how an agency collects, verifies, and manages attributes to establish and maintain enterprise identities for employees and contractors. |
 |
Credential Management is how an agency issues, manages, and revokes credentials bound to enterprise identities. |
 |
Access Management is how an agency authenticates enterprise identities and authorizes appropriate access to protected services. |
| ICAM Supporting Elements | |
 |
Federation is the technology, policies, standards, and processes that allow an agency to accept digital identities, attributes, and credentials managed by other agencies. |
 |
Governance is the set of practices and systems that guides ICAM functions, activities, and outcomes. |


