Personal Security and Identity Awareness
Pre-Decisional Draft
The following document is a Pre-Decisional Draft and should not be interpreted as a finalized rule.
Enhancing Your Security: The PDD™ Framework
(Source: Beware the Predator, 2016, ISBN 0692775293)
How objective are you when assessing your vulnerabilities? You likely believe you’ve created a safe environment for yourself and your family, but it’s easy to overlook risks when you’re too close to the situation. Many people inadvertently create a false sense of security, mistaking the feeling of safety for actual security. To truly protect yourself and your loved ones, it’s vital to explore the distinction between feeling secure and being secure. While feeling secure is comforting, genuine security is what ultimately matters.
This is where the Prevention, Deterrence, and Defense (PDD™) framework comes into play. It helps you objectively evaluate your security posture by conceptualizing layers of protection, forming concentric rings of increasing security around your life and family. The closer you get to your core—the things and people you value most—the stronger your protective measures must be. Security can seem overwhelming, but the PDD™ framework simplifies it by providing an organized approach to assess and enhance your security strategy. This process applies to every aspect of your life, regardless of the specific circumstances addressed in this guide.
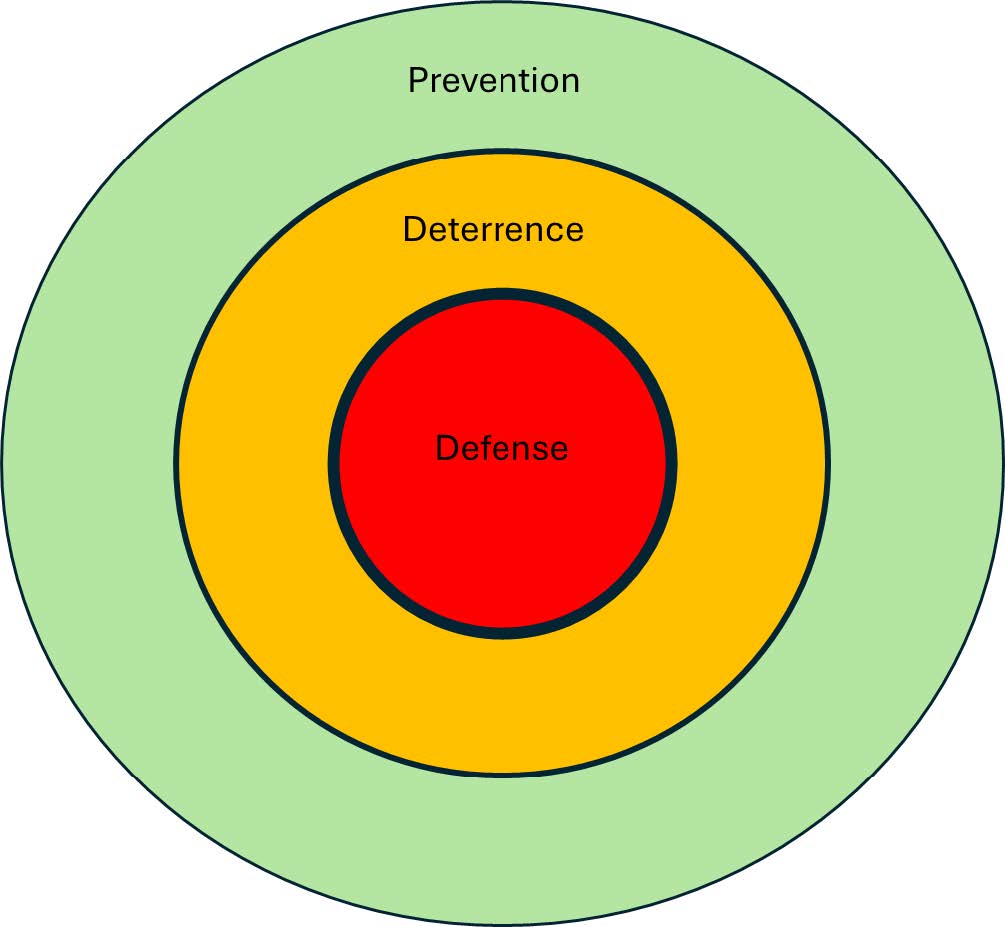
The PDD™ Framework Explained
The PDD™ concept is visualized as a series of concentric rings, with you and your family at the center. Each ring represents an opportunity to identify and counter a predator’s approach before it becomes a direct threat. Think of it as a virtual barrier, designed to delay, discourage, and defend against potential attacks.
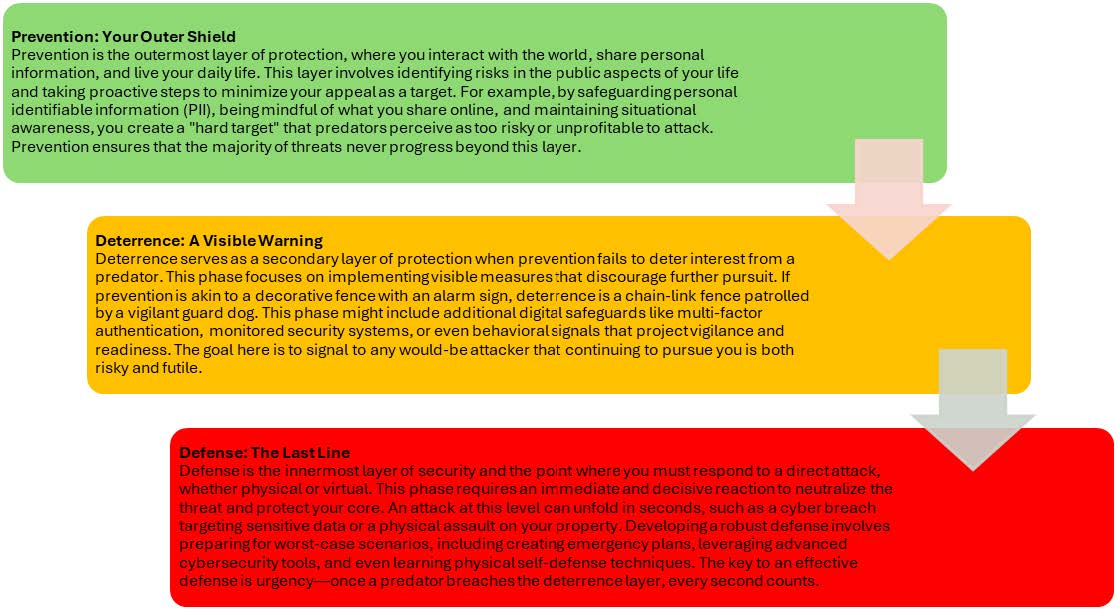
Building Your Security Posture
The PDD™ framework not only organizes your approach to security but also instills a mindset of proactive vigilance. By integrating these principles into your daily life, you enhance your ability to anticipate and counter threats at every level. The ultimate goal is to ensure multiple opportunities to disrupt a predator’s approach before they reach the critical point of defense.
Remember, security is not a one-time effort—it’s a dynamic process that evolves with your circumstances and the changing nature of threats. Apply the PDD™ concept to all aspects of your life, from your digital presence to your physical environment. By doing so, you’ll build a comprehensive security posture that bridges the gap between feeling secure and being secure.
Conducting a personal security assessment involves evaluating both your physical and digital security posture. Below are steps and examples to help the average citizen protect themselves.
-
Make a list of personal data stored online, such as passwords, financial details, and medical records. Use a password manager to audit and update weak or reused passwords. Check cloud storage services like Google Drive and iCloud for sensitive files and ensure they are encrypted. Encrypting backups and ensuring they are stored securely, such as on external drives, is also critical. Regularly test these backups to ensure data integrity and accessibility.
-
Check the visibility of your social media posts and profiles. Remove unnecessary personal information and old posts that may reveal sensitive details. Use tools like Social Sweepster to identify and delete potentially compromising posts. Similarly, limit tagged photos or posts by others that could inadvertently expose sensitive information. On professional platforms like LinkedIn, ensure that job descriptions and connections do not provide excessive insight into your role or access to critical systems.
-
Use antivirus software, VPNs, and firewalls to secure devices and connections. Install a free antivirus program like Avast and a VPN like ProtonVPN for secure browsing. Use browser extensions like HTTPS Everywhere to ensure encrypted connections on all websites. Avoid using public Wi-Fi without a VPN, as it leaves your data vulnerable to interception. For critical tasks like online banking, always use a trusted, private network.
-
Use websites like Have I Been Pwned or monitor for leaked information using Google Alerts with your name. If your email appears in a data breach, update all associated passwords immediately. Set up account activity notifications where possible to monitor unauthorized logins. Platforms like Google and Apple provide activity logs that detail recent access locations and devices, allowing users to identify unauthorized activity.
-
Search your name on Google to see what information is readily available about you. Request removal of sensitive details where possible. Use privacy services like DeleteMe to regularly scan and remove personal data from online databases. Some governments provide tools for citizens to remove personal information, such as voter registration details, from public records. These services often require proof of identity but can significantly reduce exposure.
-
Avoid sharing your live location on social media unless necessary. Instead of tagging your current location at a coffee shop, post about it after you leave. Disable location services for non-essential apps to prevent unintentional sharing of your whereabouts. Be cautious with apps that request access to location data unnecessarily, as this information can be exploited by attackers or shared with third parties without your consent.
-
Security is an ongoing process. Periodically review your digital and physical security measures to adapt to new threats. Set a calendar reminder every six months to update passwords, review social media privacy settings, and test home security systems. Stay informed about emerging threats by following trusted cybersecurity blogs or government advisories. Engage with community organizations or local cybersecurity groups to share tips and learn from others.
Best Security Practices for Social Media and Managing Publicly Available Information
In an increasingly connected world, social media platforms play a central role in our personal and professional lives. However, they also pose significant risks if not used responsibly. Understanding best practices for using social media and managing publicly available information is crucial to maintaining personal security and building a strong outer shield.
-
Avoid sharing sensitive details like your full address, phone number, or travel plans. Cybercriminals can use this information for identity theft, stalking, or burglary. Instead of posting, “Heading to Hawaii for two weeks,” share photos of your trip after you’ve returned. Additionally, avoid listing details such as your children’s schools, work hours, or daily routines, as these can be exploited for targeted crimes. Consider anonymizing family-related information or keeping it within a trusted circle to further reduce risk.
-
Adjust privacy settings to control who can view your posts, photos, and personal information. On platforms like Facebook, you can use the “Friends Only” setting for posts and ensure your contact details are hidden from public view. Regularly review settings as platforms often update them without clear notifications. Performing a privacy checkup every few months helps ensure your information stays protected. On platforms like Instagram and LinkedIn, restrict who can follow or connect with you and audit your existing list of connections to ensure they align with your preferences.
-
Only accept friend or connection requests from people you know. Attackers often use fake profiles to gather information about potential targets. If you receive a request from someone claiming to be a coworker but their profile has minimal information, verify their identity through another channel. Be aware of mutual connections—just because someone is a friend of a friend doesn’t mean they’re trustworthy. Consider reporting suspicious accounts to the platform to help improve overall security for all users.
-
Use a different, strong password for each social media account and enable multi-factor authentication (MFA) for an extra layer of security. Combine a password manager like LastPass or Dashlane with MFA to secure your accounts. Regularly update passwords, especially after a data breach, and avoid using dictionary words, common phrases, or easily guessable personal details such as birthdays or pet names. Opt for passphrases, which are easier to remember but harder to crack, such as “Th3SunR1ses@Dawn.”
-
Regularly search for fake accounts impersonating you and report them. Use tools like Have I Been Pwned to check if your information has been exposed in data breaches. If you discover a breach involving your email, immediately change passwords for associated accounts and enable MFA. Set up alerts for new account registrations in your name or similar usernames using your email address. Additionally, use reverse image search tools like TinEye or Google Images to ensure your photos aren’t being used to create fraudulent accounts.
-
Information shared on social media or available online can be exploited for malicious purposes. For example, attackers can use publicly available information, such as your employer or hobbies, to craft convincing phishing emails. Publicly sharing your location can make you a target for crimes like theft or stalking. Posting a picture of your expensive new TV along with your location tag could attract burglars. Additionally, posting opinions or sensitive work information can lead to disciplinary action or damage to your reputation. Regularly audit your digital footprint by searching your name and associated details to identify potential vulnerabilities.
Operational and Practical Digital Security Hygiene
In today’s digital world, protecting yourself online doesn’t have to be complicated. Simple habits and tools can significantly reduce your risk of falling victim to cyber threats. Here are some best practices anyone can follow, with real-world examples to get you started.
-
Use Strong, Unique Passwords
One of the easiest ways hackers gain access to accounts is by guessing or stealing passwords. Avoid using simple passwords like “password123” or reusing the same password across multiple sites.
Tactical Example: Use a free password manager like Bitwarden or LastPass to create and store strong, unique passwords for each account. A strong password should be at least 12 characters long and include a mix of letters, numbers, and symbols. For instance, instead of “John2023,” try “JoHn$ecUr3!2023.”
-
Enable Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
Tactical Example: Turn on MFA for critical accounts like email, banking, and social media. Platforms like Gmail, Facebook, and Amazon have easy-to-follow guides to enable MFA. This way, even if someone steals your password, they can’t log in without the second verification step.
-
Keep Software Updated
Outdated software often has security flaws that hackers can exploit. Regular updates fix these vulnerabilities.
Tactical Example: Enable automatic updates on your devices, including smartphones, computers, and applications. For example, on Windows, go to Settings > Update & Security > Windows Update to ensure your system is always up to date.
-
Be Cautious with Links and Attachments
Phishing scams trick you into clicking malicious links or downloading harmful files. Always verify before interacting with suspicious content.
Tactical Example: If you receive an unexpected email claiming to be from your bank, don’t click any links. Instead, go to your bank’s website directly by typing the URL into your browser or call their customer service department. Use free online tools like VirusTotal to scan links or attachments for malware before opening them.
-
Use Public Wi-Fi Safely
Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your data.
Tactical Example: Avoid logging into sensitive accounts, like banking, while on public Wi-Fi. If you must use public Wi-Fi, use a Virtual Private Network (VPN) app like ProtonVPN or NordVPN to encrypt your connection. Many free VPN options exist for casual use.
-
Back Up Your Data Regularly
Backing up your data ensures you can recover important files if your device is lost, stolen, or infected with ransomware.
Tactical Example: Use cloud services like Google Drive or iCloud for automatic backups. For physical backups, an external hard drive updated monthly can also be a lifesaver.
-
Secure Your Home Network
Your home Wi-Fi is the gateway to all your devices. Keep it safe by changing default settings and passwords.
Tactical Example: Change your router’s default password to something strong. Set your Wi-Fi encryption to WPA3 (or WPA2 if WPA3 isn’t available) to ensure connections are secure. Many routers have step-by-step guides for this in their user manuals.
Secure Credential Management: Methods and Best Practices for Individuals
In an era of increasing cyber threats, secure credential management is essential for safeguarding digital access and protecting sensitive information. Credentials, such as usernames, passwords, and authentication tokens, are the keys to your digital identity and must be managed with care. The following are examples of secure credential management practices applicable to all individuals.
-
Use Strong, Unique Passwords
Each of your accounts should have a strong, unique password that is difficult to guess or crack. A strong password typically contains at least 12 characters, including a mix of uppercase and lowercase letters, numbers, and special symbols.
Tactical Example: Replace simple passwords like “John1234” with complex ones such as “7$K8q!Lf@X9%rH”.
Tools: Password managers like LastPass, 1Password, and Bitwarden can generate and store complex passwords securely. Apple and Android phones also have built-in password managers with these capabilities.
-
Enable Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, a biometric scan, or a hardware token.
Tactical Example: After entering a password, a user receives a one-time code via an app like Google Authenticator or by SMS to complete the login process.
Tools: Popular MFA tools include Duo Security, Microsoft Authenticator, and YubiKey.
-
Avoid Credential Reuse
Reusing the same password across multiple accounts increases your vulnerability to credential stuffing attacks. Each account should have its own unique credentials.
Tactical Example: If the password for a social media account is compromised, it should not also provide access to email or banking accounts.
-
Store Credentials Securely
Avoid storing your passwords in plain text or insecure locations. Use encrypted storage solutions for sensitive credentials.
Tactical Example: Instead of saving passwords in a text file, use a password manager that encrypts data.
-
Regularly Update Credentials
Change your passwords periodically and immediately after a breach. Set calendar reminders to update critical credentials every 90 days.
Tactical Example: Rotate administrative passwords for corporate systems every three months.
-
Use Passphrases for Enhanced Security
Passphrases are longer strings of words or phrases that are easier to remember but hard to crack. They provide an alternative to complex passwords.
Tactical Example: A passphrase like “PurpleElephant$Dances!OnMars” is memorable and secure.
-
Monitor for Credential Exposure
Regularly check if your credentials have been compromised in data breaches using services like Have I Been Pwned.
Tactical Example: If an email address is found in a breach, update associated passwords immediately.
-
Use Hardware-Based Authentication
Hardware tokens, such as YubiKeys or smart cards, provide physical authentication factors that are highly secure.
Tactical Example: Plugging a YubiKey into a computer’s USB port to authenticate a login adds an additional security layer.
Secure Credential Management: Methods and Best Practices in an Organization
While strengthening your personal security posture using the above best practices is essential, it’s equally important to consider how security practices extend into your professional environment. Whether you’re part of a small team or a large organization, managing credentials securely plays a critical role in protecting both individual and enterprise data. Depending on your role within an organization, you can use and promote the following best practices:
-
Educate Users on Security Awareness
Conduct regular training sessions on recognizing phishing attempts, the importance of strong passwords, and the use of MFA.
-
Centralize Credential Management
Use enterprise-grade identity and access management (IAM) solutions, such as Okta or Azure AD, to centralize credential storage and enforce security policies.
-
Automate Password Expiry and Rotation
Set automated policies for password expiry and ensure that your users rotate passwords regularly.
-
Restrict Privileged Account Access
Limit access to critical systems to only those in your organization who need it and regularly review access permissions.
-
Implement Recovery Protocols
Ensure there are secure processes for credential recovery, such as requiring identity verification before resetting passwords.
-
Conduct Regular Security Audits
Periodically review and update your organization’s credential management practices to stay ahead of evolving threats.
-
Adopt Zero-Trust Principles
Implement continuous monitoring of user behavior to detect anomalies, such as login attempts from unusual locations, and limit trust in any single authentication factor.
Recommendations for Multi-Layered Protection of Digital Personas
In the digital age, protecting digital personas is essential for safeguarding both individual and organizational security. Digital personas encompass user credentials, personal information, professional identifiers, and behavioral data, making them prime targets for cyberattacks. The following are recommendations for implementing multi-layered protection in your organization, best practices for government personnel, and strategies for anomaly detection to mitigate risks of compromised identities.
Multi-Layered Protection for Digital Personas
-
Content Security Policies (CSPs):
CSPs prevent the execution of unauthorized scripts, reducing the risk of data theft and injection attacks.
Implementation:
- Define and enforce a restrictive CSP that permits only trusted sources for scripts, stylesheets, and media.
- Regularly review and update CSP rules to adapt to emerging threats.
Tactical Example: A CSP can block third-party scripts that attempt to access sensitive profile data or inject malicious payloads.
-
Secure Content Delivery Network (CDN) Management:
A Content Delivery Network (CDN) is a distributed network of servers strategically located around the world that store cached copies of website content, enabling faster and more reliable delivery of digital information to users by serving content from the geographically nearest server. CDNs improve performance but can be exploited to distribute malicious content.
Implementation:
- Use Subresource Integrity (SRI) to verify the integrity of CDN-hosted assets.
- Collaborate with CDN providers to ensure robust security practices, including traffic monitoring and incident response plans.
- Restrict CDN access to authorized IP ranges and enforce HTTPS for secure communication.
Tactical Example: Agencies can monitor CDN activity to detect unauthorized changes to hosted assets, such as altered scripts.
-
Regular Audits to Detect Unauthorized Changes:
Audits identify anomalies in digital persona data and unauthorized modifications to resources.
Implementation:
- Conduct periodic reviews of profile data, permissions, and hosted content.
- Use version control and checksums to ensure data integrity.
Tactical Example: Auditing email signature settings across a department can prevent the misuse of altered identifiers for phishing campaigns.
Best Practices for Government Personnel
-
Use Secure Single Sign-On (SSO):
SSO simplifies authentication while centralizing security controls.
Implementation:
- Deploy enterprise-grade SSO solutions with multi-factor authentication (MFA).
- Limit SSO access to verified applications and enforce strong password policies.
Tactical Example: Using Okta or Azure AD with biometric authentication enhances the security of login sessions.
-
Limit Persona Information Exposure:
Minimizing publicly available persona details reduces the attack surface for social engineering and impersonation attempts.
Implementation:
- Avoid sharing job titles, email addresses, and direct contact information on public platforms.
- Use pseudonyms or generic titles for public-facing accounts where appropriate.
Tactical Example: Replacing direct email links with secure contact forms on official websites protects against spam and phishing.
-
Set Stringent Permissions for CDN Access:
Government agencies and large institutions increasingly deploy CDNs to ensure rapid, secure, and resilient access to critical digital services, particularly during high-traffic events or potential cyber incidents that could overwhelm traditional web infrastructure. Restricting access prevents unauthorized modifications to profile data and hosted content.
Implementation:
- Use role-based access control (RBAC) to manage permissions for modifying CDN-hosted resources.
- Monitor access logs for unusual activity.
Tactical Example: Limiting administrative privileges to specific personnel prevents accidental or malicious changes to critical CDN assets.
Persona-Focused Anomaly Detection and Behavioral Monitoring
-
Implement Behavioral Monitoring Systems:
These systems identify unusual activity patterns that may indicate compromised digital identities.
Implementation:
- Deploy tools that analyze login times, IP addresses, and session durations to detect anomalies.
- Flag behaviors such as multiple login attempts from different locations or devices within a short timeframe.
Tactical Example: Monitoring for login attempts from foreign IPs outside normal working hours can help identify unauthorized access.
-
Automate Alerts for Persona-Specific Risks:
Automated alerts ensure rapid response to potential threats.
Implementation:
- Configure alerts for changes to key identifiers, such as job titles or email signatures.
- Use machine learning algorithms to refine detection capabilities based on historical data.
Tactical Example: An alert triggered by an unauthorized update to a government official’s contact information can prevent the misuse of altered details.
-
Integrate Zero-Trust Principles:
Continuous verification ensures that access is granted only to authorized users and devices.
Implementation:
- Require MFA for all access attempts and validate device compliance before granting entry.
- Regularly reassess trust levels based on real-time data.
Example: Requiring re-authentication for sensitive actions, such as exporting profile data, adds an additional layer of security.
Conclusion
Security is not a static state—it is a continuous, evolving process that requires vigilance, adaptation, and strategic implementation. The Prevention, Deterrence, and Defense (PDD™) framework provides a structured approach to assessing and enhancing security across all aspects of life, from personal safety to digital resilience. By integrating its principles, individuals can systematically build protective layers, reducing their exposure to threats while increasing their ability to detect and respond to adversarial actions.
In an era where digital and physical risks intersect, proactive security measures are critical. Implementing best practices in credential management, digital hygiene, and social media awareness ensures that personal and professional information remains safeguarded. From employing strong, unique passwords and multi-factor authentication to limiting publicly available information and monitoring for anomalies, each step fortifies the security posture against evolving threats.
The key takeaway is clear: feeling secure is not the same as being secure. True security comes from objectivity, assessment, and action. By applying the PDD™ framework and embracing a multi-layered, adaptive security mindset, individuals can protect what matters most—transforming security from a perceived sense of safety into a tangible, fortified reality.


