CDN Attack Vectors and Mitigation
Pre-Decisional Draft
The following document is a Pre-Decisional Draft and should not be interpreted as a finalized rule.
Compromised CDNs and Unauthorized Access
When CDNs are compromised, attackers can bypass security controls that depend on trusted content delivery systems. This enables:
- Access to Secure Areas:
- Methodology: Attackers inject malicious scripts into CDN-distributed assets, which are then loaded onto government portals or internal systems. This can lead to the theft of session tokens or login credentials.
- Implications: Unauthorized access to secure areas of government networks can allow attackers to exfiltrate classified information, install backdoors, or disrupt operations.
- Behavior Monitoring:
- Methodology: By embedding trackers or keyloggers in CDN-distributed resources, attackers can monitor user behaviors on government platforms.
- Implications: Tracking user habits, login patterns, and activity logs can help attackers map organizational workflows and identify potential weaknesses for exploitation.
- Manipulation of Identifiers:
- Methodology: Altering scripts or cached content on a CDN enables attackers to modify data fields like email signatures, job titles, and other visible identifiers.
- Implications: Misinformation can be spread through altered identifiers, damaging trust and creating confusion within government agencies and among external stakeholders.
Risks to Digital Persona Data
The types of data stored and accessed via CDNs often include elements of digital personas that attackers can exploit:
- Email Signatures:
- Threat: Compromised CDNs can distribute scripts that replace legitimate email signatures with fraudulent ones, redirecting recipients to phishing sites or towards malicious attachments.
- Implications: Recipients may unknowingly engage with attackers, leading to further compromise within or beyond the organization.
- Job Titles and Contact Information:
- Threat: Attackers can manipulate job titles and contact details to impersonate high-ranking officials or key personnel.
- Implications: Such impersonations can facilitate spear-phishing attacks, where adversaries exploit the credibility of altered identifiers to extract sensitive information or funds.
- Identity Markers:
- Threat: Other identity markers, such as profile photos, department names, and certifications, can be altered to mislead users.
- Implications: Manipulated identity markers can erode trust in official communications and damage the reputations of individuals and agencies.
Enabling Social Engineering and Phishing Campaigns
Compromised CDNs create opportunities for attackers to craft highly convincing social engineering and phishing campaigns:
- Enhanced Credibility:
- By leveraging modified identifiers and authentic-looking content served through trusted CDNs, attackers can increase the likelihood that their phishing attempts will succeed.
- Widespread Distribution:
- CDNs’ global reach allows attackers to spread malicious content efficiently, targeting both government personnel and external collaborators with a single effort.
- Dynamic Attacks:
- Real-time manipulation of CDN-hosted assets enables attackers to adapt their tactics to evade detection and sustain long-term campaigns.
Mitigation Strategies
- Strengthen CDN Security:
- Enforce Subresource Integrity (SRI) to validate the integrity of CDN-delivered resources.
- Collaborate with CDN providers to ensure robust security practices and incident response capabilities.
- Enhance Monitoring and Auditing:
- Deploy tools to monitor CDN traffic and detect anomalies in real-time.
- Conduct regular audits of CDN configurations and cached content.
- Educate Personnel:
- Train government employees to recognize signs of phishing and social engineering.
- Encourage verification of email signatures, job titles, and other identifiers before responding to requests.
- Implement Multi-Layered Security:
- Use multi-factor authentication (MFA) for access to sensitive systems.
- Segment networks to contain potential breaches.
Analysis of Attack Methods Targeting CDNs
Content Delivery Networks (CDNs) are critical to ensuring fast and reliable web services. However, their ubiquity and central role in web infrastructure make them attractive targets for attackers. This document provides a detailed analysis of attack methods, including supply chain attacks, cache poisoning, and DNS spoofing, which can exploit CDNs to spread malicious scripts and compromise digital personas.
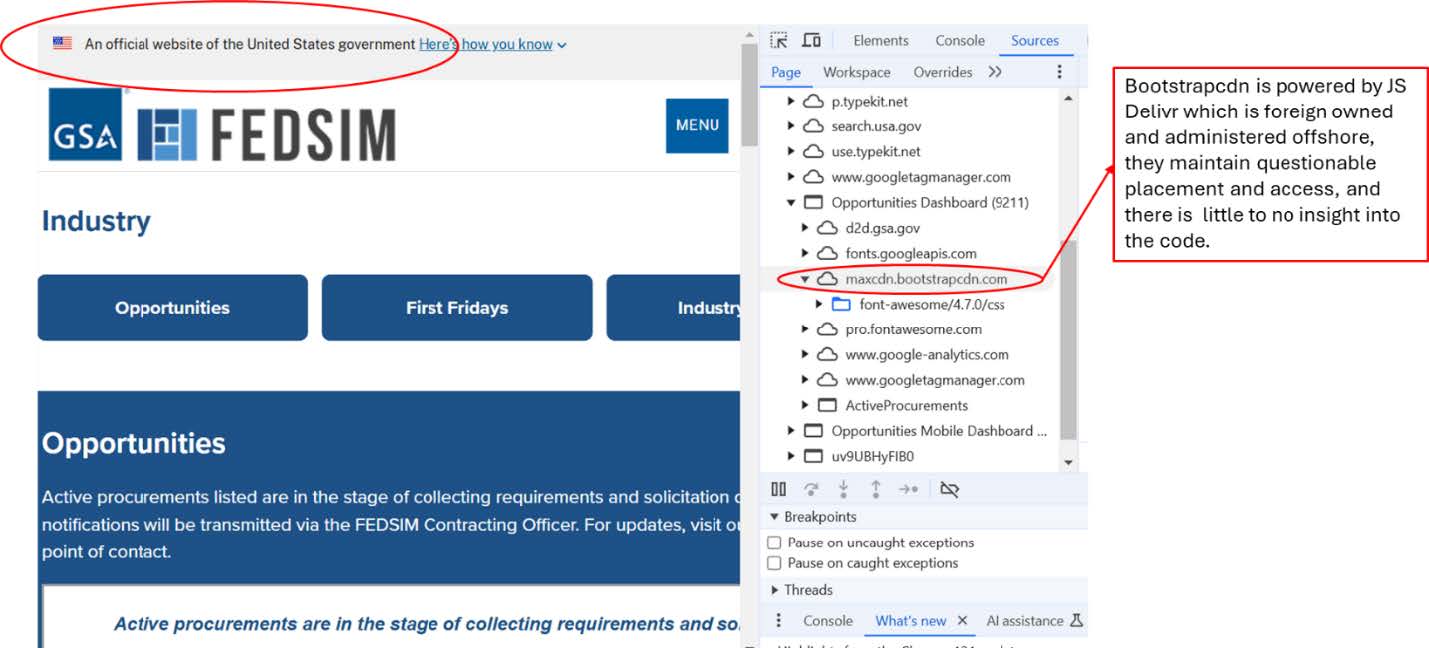
Supply Chain Attacks
Supply chain attacks exploit vulnerabilities in third-party software or services integrated into a CDN’s ecosystem. Attackers infiltrate these dependencies to inject malicious scripts or compromise the integrity of content served by the CDN.
Methodology:
- Exploiting Trust in Whitelisted Traffic: Many organizations whitelist CDN traffic to ensure uninterrupted delivery of assets. Attackers leverage compromised CDN endpoints or assets to bypass firewalls and intrusion detection systems (IDS), which often overlook trusted CDN IP ranges.
- Impact: Blind spots in security allow malicious scripts to pass through without scrutiny.
- Obfuscating Malicious Payloads: Attackers inject malicious payloads into CDN-hosted resources such as JavaScript libraries and images.
- Impact: Traditional web application firewalls (WAFs) struggle to detect malicious scripts embedded in legitimate-looking CDN-hosted resources.
- Evading Intrusion Detection Systems: CDN-based attacks pair malicious traffic with high volumes of legitimate requests.
- Impact: Malicious activities, such as credential theft or data exfiltration, are masked by legitimate traffic.
- Manipulating Caching Mechanisms: Attackers poison CDN caches to distribute altered or malicious content directly to end-users.
- Impact: Cache poisoning compromises systems by serving malicious versions of critical resources.
Technical Examples:
- Malware Delivery via Whitelisted Traffic:
- Attackers compromise a JavaScript library hosted on a popular CDN, injecting malware that executes on client systems upon loading. Firewalls and WAFs fail to block this traffic due to implicit trust.
- Case Study: The 2018 Magecart attack group compromised JavaScript libraries to steal payment data from e-commerce platforms.
- Impact: Widespread data theft and financial losses.
- Data Exfiltration Using CDN Endpoints:
- Compromised CDN-hosted resources embed data-exfiltration scripts, stealing sensitive data such as login credentials.
- Example: Attackers intercept user inputs from government login portals using a compromised analytics script.
- Impact: Espionage and operational disruption.
- Credential Handling Manipulation:
- Attackers alter authentication scripts cached by a CDN to redirect credentials to malicious endpoints.
- Case Study: The 2018 MyEtherWallet DNS spoofing attack redirected users to phishing sites, resulting in stolen cryptocurrency wallets.
- Impact: Identity theft and financial repercussions.
Cache Poisoning
Cache poisoning exploits vulnerabilities in CDN caching mechanisms to serve malicious or altered content to end-users.
Methodology:
- Attackers craft HTTP requests to the CDN, tricking it into caching malicious content. Subsequent requests retrieve this poisoned cache, spreading malicious scripts to users.
Impacts:
- Users receive modified content that can execute malicious scripts or redirect them to phishing sites.
- Altered content can impersonate digital personas, leading to fraudulent activities.
Technical Example:
- In 2018, researchers demonstrated cache poisoning vulnerabilities in major CDNs, allowing attackers to distribute altered web pages to users. (Source: “Practical Cache Poisoning,” 2018)
Mitigation Strategies:
- Implement strict cache key normalization to prevent exploitation.
- Use HTTPS with secure headers to reduce malicious cache manipulation.
- Regularly purge and validate cached content for integrity.
DNS Spoofing
DNS spoofing, or DNS cache poisoning, involves redirecting users to malicious servers by corrupting DNS entries.
Methodology:
- Attackers inject forged DNS responses into a resolver’s cache, replacing the IP address of a legitimate CDN edge server with one they control.
Impacts:
- Users receive tampered content, including malware or phishing scripts.
- Attackers impersonate individuals by serving fake profiles or credentials via altered content.
Technical Example:
- The 2018 MyEtherWallet DNS spoofing attack redirected users to a phishing site, resulting in significant financial losses.
Mitigation Strategies:
- Implement DNSSEC to authenticate DNS responses.
- Use certificate pinning and HTTPS to ensure secure connections between clients and CDN servers.
Combining Attack Methods for Greater Impact
Attackers often combine these methods to maximize their reach:
- Example: An attacker compromises a third-party library (supply chain attack), poisons the CDN cache with malicious versions of the library, and uses DNS spoofing to redirect users to malicious servers.
- Impact: Wide distribution of malware, phishing scripts, and compromised user data.
Mitigation Strategies for Comprehensive Defense:
- Network-Level Protections:
- Deploy robust firewalls and IDS to monitor suspicious activities targeting CDN infrastructure.
- Application-Level Protections:
- Enforce Content Security Policies (CSPs) to restrict unauthorized scripts.
- Regularly update and patch CDN configurations.
- User Awareness and Education:
- Train users to recognize phishing attempts and verify HTTPS connections.
How to Prevent Malicious JavaScript Injection via CDNs
- Secure Infrastructure:
- Use multi-factor authentication (MFA) for admin access.
- Regularly audit and patch vulnerabilities in CDN software and servers.
- Monitor and Validate Files:
- Use hashing mechanisms to verify the integrity of files served.
- Implement automated tools to detect unauthorized changes to hosted files.
- Segregate Access:
- Limit administrative access and ensure strict access controls.
For Website Owners:
- Use Subresource Integrity (SRI):
- Add an SRI attribute to
<script>tags to verify the hash of a loaded file. If the file is altered, the browser will reject it. - Example:
<script src="https://cdn.example.com/script.js" integrity="sha384-abc123" crossorigin="anonymous"></script>
- Add an SRI attribute to
- Content Security Policy (CSP):
- Implement CSPs to restrict the execution of unauthorized scripts. For example:
- Content-Security-Policy: script-src ‘self’ https://trusted-cdn.com;
- Implement CSPs to restrict the execution of unauthorized scripts. For example:
- Use Local Hosting for Critical Scripts:
- Host critical JavaScript files locally rather than relying on external CDNs.
- Monitor CDN Activity:
- Regularly verify the integrity of scripts loaded from the CDN.
For End Users:
- Enable Browser Protections:
- Use modern browsers with anti-phishing and anti-malware features enabled.
- Use Security Extensions:
- Tools like NoScript can block unnecessary JavaScript execution.
Detecting and Responding to Malicious Injections
- Detection:
- Regularly audit network traffic for unexpected connections to unknown domains.
- Use automated scanning tools to identify injected scripts on web pages.
- Response:
- If a compromise is detected, immediately revoke CDN credentials, replace the affected files, and notify affected parties.
- Conduct a post-mortem analysis to prevent recurrence.
Case Studies of CDN-Based Compromises
- Cloudflare and the Cloudbleed Incident (2017):
- Overview: A bug in Cloudflare’s edge servers leaked sensitive data, including cookies and tokens, to random HTTP requests.
- Impact: Exposed data enabled account takeovers and social engineering campaigns.
- Mitigation: Rigorous testing of edge server code and improved session management practices.
- MyEtherWallet DNS Spoofing (2018):
- Overview: Attackers redirected users to phishing sites using DNS spoofing.
- Impact: Users lost over $150,000 in cryptocurrency.
- Mitigation: Deployment of DNSSEC and HTTPS with strong certificate pinning.
- Social Engineering via Compromised CDNs (2020):
- Overview: Attackers embedded malicious macros in altered documents distributed via compromised CDNs.
- Impact: Stolen sensitive information, including credentials and personal identifiers.
- Mitigation: Robust monitoring of CDN content and user education.
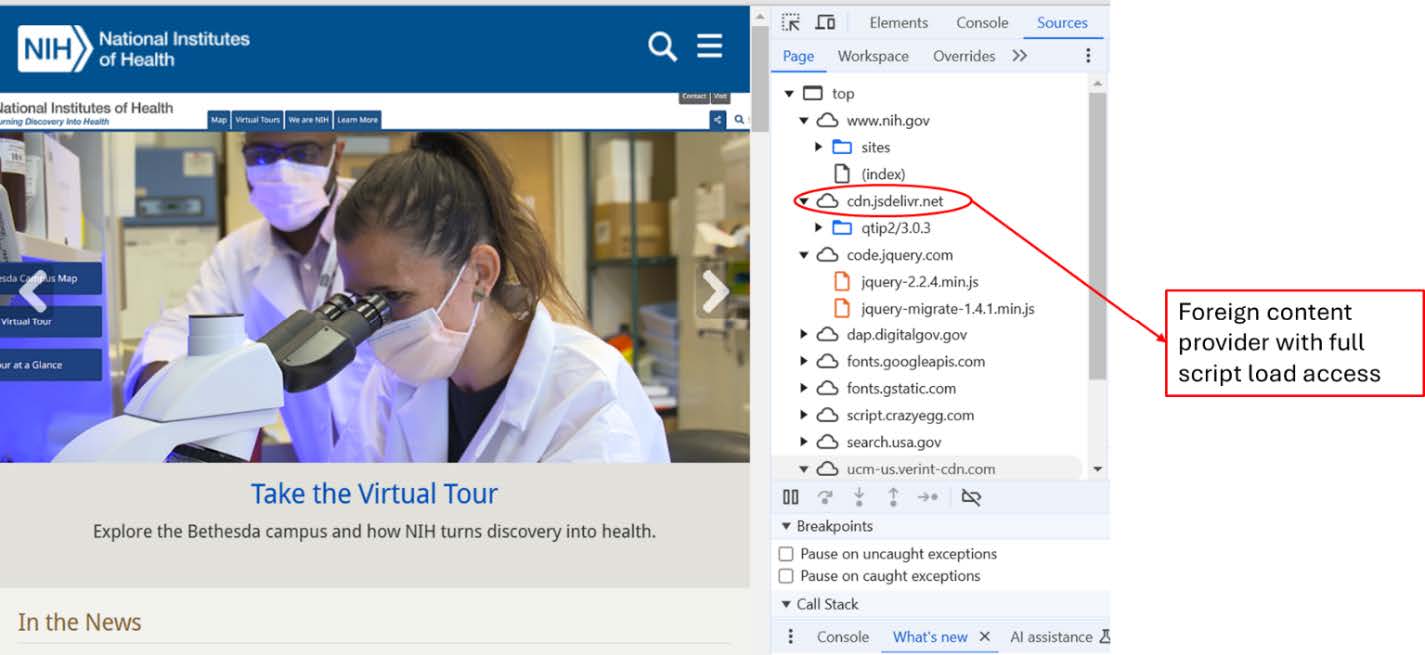
Implications for Government and Organizational Security
Compromised CDNs pose significant risks to government and organizational security by enabling attackers to bypass protections, access secure areas, monitor user behavior, and manipulate identifiers. To mitigate these risks, organizations must:
- Prioritize zero-trust principles.
- Implement robust monitoring and integrity validation mechanisms.
- Educate users about the risks associated with compromised CDNs.
By adopting these strategies, organizations can reduce the impact of CDN-based attacks and safeguard their digital infrastructure.
Deception as a Defensive Security Posture:
In an era of increasingly sophisticated cyber threats, empowering citizens with effective, low-cost methods to detect and defend against malicious activity is paramount. Deception technology—a strategy traditionally utilized by enterprises and government agencies—can be adapted and scaled for everyday use by individuals and small organizations. By leveraging readily available and cost-effective tools, citizens can implement deception strategies to enhance their defensive security posture
The Role of Deception in Cyber Defense
Deception techniques in cybersecurity involve creating false information, systems, or environments to mislead attackers. These tactics increase the cost and complexity of executing successful cyberattacks while providing defenders with valuable insights into attacker behavior. For citizens, implementing deception technology can deter opportunistic threats, such as phishing attempts, ransomware, and unauthorized system access, by confusing and frustrating adversaries.
Cost-Effective Deception Methods
- Honeyfiles and Honeytokens
- Description: These are decoy files or data objects placed within a user’s system to appear valuable to an attacker.
- Implementation:
- Start by identifying areas in your system where an attacker might look for sensitive information, such as document folders or email archives.
- Use free tools like Canarytokens to create honeytokens. These tokens can take the form of fake credentials, URLs, or files. For example, generating a “passwords.txt” file with embedded tracking capabilities.
- Place these decoys strategically within your file structure to maximize their likelihood of being accessed by an attacker.
- Configure notifications to alert you if the honeyfile or token is accessed, providing early warning of suspicious activity.
- Decoy Networks
- Description: Setting up fake network environments to divert attackers from actual assets.
- Implementation:
- Use a secondary router or inexpensive devices like Raspberry Pi to create a separate decoy network. Assign it a plausible name, such as “Home_WiFi_Guest.”
- Ensure that the decoy network’s settings mimic those of a legitimate network by using typical SSID names and enabling basic security settings.
- Deploy simple decoy servers or IoT devices that attackers might target. These can include dummy login portals or fake file shares.
- Monitor traffic on the decoy network using tools like Wireshark or Suricata to detect unauthorized access attempts and gather intelligence on attacker methods.
- Browser and Email Deception
- Description: Using fake accounts or obfuscating personal data to protect against phishing and other email-based threats.
- Implementation:
- Create burner email addresses using services like ProtonMail, 10MinuteMail, or Guerrilla Mail to avoid exposing your primary email address to untrusted platforms.
- Use browser extensions such as Privacy Badger, uBlock Origin, or Ghostery to block trackers and mask online behavior, making it harder for attackers to profile you.
- Maintain a set of fake online personas for situations where sharing real personal information is unnecessary, such as participating in forums or registering for services.
- Configure spam filters aggressively and report phishing attempts to your email provider to help improve collective defenses.
- Behavioral Honeypots
- Description: Identifying and monitoring unusual activities by employing traps that only malicious actors would trigger.
- Implementation:
- Enable multi-factor authentication (MFA) on all accounts, but monitor for any unusual attempts to bypass it. Platforms like Google, Microsoft, Amazon, and social media sites such as Facebook and Twitter often provide detailed account activity logs and real-time notifications for unauthorized login attempts. Leverage these features to stay informed about potential breaches.
- Use low-cost intrusion detection systems (IDS) like Snort or Zeek to monitor traffic on your home network. These tools can flag suspicious behaviors such as repeated login attempts or data exfiltration patterns.
- Set up traps such as fake login forms on non-critical devices. For example, use free or low-cost software to create a login screen that mimics legitimate services but does not grant access and instead records all interaction attempts, such as usernames, passwords, and timestamps. Deploy these traps on devices not critical to your operations, like secondary laptops or virtual machines, and regularly monitor the logs for signs of unauthorized activity.
- Leverage operating system features like Windows Defender’s Controlled Folder Access to detect and block ransomware activities in decoy directories.
Enhancing Citizen Awareness
Education is critical in enabling citizens to effectively use deception techniques. Workshops, online tutorials, and community-driven cybersecurity programs can demystify these tools and promote their widespread adoption. Government agencies and private organizations should collaborate to provide accessible resources, templates, and guidelines tailored to individuals and small businesses.
Conclusion
Content Delivery Networks (CDNs) are a cornerstone of modern digital infrastructure, providing enhanced performance, scalability, and security. However, the increasing reliance on CDNs introduces significant security risks when these networks are compromised. Attackers can leverage malicious JavaScript injections, cache poisoning, and DNS spoofing to bypass security controls, exfiltrate sensitive data, manipulate digital identities, and enable large-scale social engineering attacks. These vulnerabilities highlight the urgent need for a proactive, defense-in-depth approach to securing CDN infrastructure.
To mitigate these threats, organizations must adopt comprehensive security strategies that include Subresource Integrity (SRI), Content Security Policies (CSPs), continuous traffic monitoring, and multi-factor authentication (MFA). Strengthening partnerships with CDN providers, implementing real-time anomaly detection, and enforcing zero-trust security principles will be critical in preventing CDN-based cyber threats. Furthermore, organizations should educate personnel on identifying phishing attempts, verifying digital identifiers, and recognizing signs of CDN-based attacks.
As adversaries continue to exploit trusted delivery systems, deception techniques—such as honeytokens, behavioral honeypots, and fake credentials—can serve as valuable tools for detecting unauthorized access and misleading attackers. Additionally, government agencies and enterprises must prioritize resilience by segmenting networks, restricting CDN permissions, and conducting regular security audits.
Ultimately, securing CDNs requires a shift from passive reliance to active threat mitigation. By integrating layered security defenses, deception methodologies, and rigorous validation mechanisms, organizations can ensure that CDNs remain a reliable, secure component of digital infrastructure rather than a vector for large-scale compromise. In a rapidly evolving cyber threat landscape, prioritizing CDN security is not optional—it is a strategic imperative.


