CDN Reliability, Assumptions, and Vulnerabilities
Pre-Decisional Draft
The following document is a Pre-Decisional Draft and should not be interpreted as a finalized rule.
A Content Delivery Network (CDN) is a system of distributed servers strategically placed across various geographic locations to deliver digital content—such as websites, videos, applications, and other data—quickly and reliably to users. By caching content closer to the end user, CDNs reduce latency, improve loading times, and enhance the overall user experience. They also help balance traffic loads, ensuring that no single server is overwhelmed during spikes in demand. CDNs are commonly used for streaming media, e-commerce platforms, and large-scale web applications. Additionally, they provide an extra layer of security by mitigating Distributed Denial of Service (DDoS) attacks and offering encryption protocols to protect data in transit.
Content Delivery Networks (CDNs) are integral to modern web infrastructure, offering improved performance, scalability, and security. However, they are often assumed to be infallible, which can cause people to overlook the potential vulnerabilities that cyber actors can exploit to access individual digital profiles, credentials, and sensitive information. Below, we examine these assumptions and associated risks.
CDNs are often assumed to guarantee availability and data security, but this function also introduces vulnerabilities. While CDNs mitigate Distributed Denial of Service (DDoS) attacks, targeted assaults on specific edge nodes can overwhelm localized services, exposing redundancy gaps. During failover events, attackers may intercept rerouted traffic if fallback configurations are insecure. Similarly, caching, a core CDN function, carries risks like cache poisoning, where malicious actors inject harmful scripts into cached content, or the exploitation of expired cache entries to serve outdated and insecure data. These risks highlight the importance of properly managing caching policies and securing failover mechanisms to maintain service integrity.
Additional assumptions about CDN security also present challenges. While TLS/SSL encryption is widely used, outdated certificates or misconfigured HTTPS setups can expose traffic to man-in-the-middle attacks. If CDN certificates are compromised, attackers can impersonate the CDN and intercept sensitive data. Moreover, CDNs designed to shield origin servers can fail if misconfigurations, such as IP leakage or lax firewall rules, allow attackers to bypass protections. Despite offering tools like Web Application Firewalls (WAFs), CDNs may still leave systems vulnerable to advanced threats like SQL injection or zero-day attacks. These blind spots emphasize the need for proactive monitoring, robust configurations, and layered security measures to address potential exploitation.
What CDNs Provide
- Performance Optimization
- Reduced Latency: CDNs cache content closer to end-users, minimizing the physical distance data needs to travel. This ensures faster page load times for users accessing government websites or applications.
- Efficient Content Delivery: Static assets like images, videos, and documents are served quickly through CDN edge servers, reducing the load on origin servers and enhancing user experience.
- Scalability: During high-traffic events such as election periods or emergency updates, CDNs can handle spikes in demand by balancing traffic across multiple servers.
- Reliability and Availability
- High Availability: CDNs improve uptime by rerouting traffic to functioning servers if an origin server fails, ensuring uninterrupted access to critical government services.
- Load Balancing: By distributing traffic evenly, CDNs prevent server overloads that can cause downtime.
- Disaster Recovery: CDNs provide resilience against data center outages by storing cached copies of essential content in multiple locations.
- Enhanced Security
- DDoS Mitigation: CDNs can absorb and mitigate Distributed Denial of Service (DDoS) attacks by spreading traffic across a vast network of servers, protecting government infrastructure from disruption.
- Web Application Firewalls (WAFs): Many CDNs offer integrated WAFs to defend against common web application vulnerabilities such as SQL injection and cross-site scripting (XSS).
- TLS/SSL Encryption: CDNs ensure secure connections through widespread implementation of TLS/SSL certificates, safeguarding sensitive information transmitted between users and government servers.
- Cost Efficiency
- Reduced Bandwidth Costs: By serving cached content from edge servers, CDNs significantly reduce the bandwidth consumed by origin servers, lowering operational expenses.
- Optimized Resource Usage: With CDNs handling static content delivery, origin servers can focus on processing dynamic requests, optimizing resource allocation and reducing the need for frequent hardware upgrades.
- Support for Modern Applications
- Edge Computing: CDNs facilitate edge computing capabilities, enabling real-time processing of data closer to the user. This is particularly beneficial for latency-sensitive applications, such as public safety systems and live data dashboards.
- API Management: Many government applications rely on APIs. CDNs can cache API responses, improving the performance and scalability of applications that serve large-scale user bases.
- Mobile Optimization: CDNs provide tools to optimize content for mobile devices, ensuring seamless experiences for citizens accessing services via smartphones and tablets.
- Compliance and Data Sovereignty
- Geographical Control: CDNs offer options to restrict data storage and transfer to specific regions, aiding compliance with data sovereignty regulations like GDPR or domestic privacy laws.
- Auditability: Leading CDN providers maintain detailed logs and monitoring tools, helping governments meet transparency and accountability standards.
When a Content Delivery Network (CDN) is compromised, however, malicious JavaScript injection can have widespread consequences because the CDN serves scripts to many websites, making it an effective distribution method for attackers.
Exploitation on the Glass
Exploitation on the glass at runtime refers to attacks that target the user interface (UI) layer of an application while it is actively running and being used. The term “glass” metaphorically represents the screen or the visible layer of the application where user interactions occur, such as clicking buttons, typing into fields, or viewing dynamic content. Unlike server-side exploits, this type of attack occurs client-side, typically in a user’s browser or application session. Modern antivirus programs do not monitor or do discovery of threat vectors on the glass.
Most modern applications use client-side code (like JavaScript) to provide real-time, interactive experiences. However, if the UI layer isn’t properly secured, attackers can exploit weaknesses at runtime — meaning during live use — to manipulate data, visuals, or user interactions.
Examples

Why It’s Important

CDN Assumptions
Assumption 1: CDNs Always Ensure Availability
CDNs are designed to enhance availability through redundant servers and failover mechanisms. However, attackers can exploit this assumption by using:
- DDoS Attacks Targeting CDN Nodes: While CDNs mitigate Distributed Denial of Service (DDoS) attacks, targeted assaults on specific edge nodes can overwhelm localized services, causing disruptions and exposing gaps in redundancy.
- Exploiting Failover Gaps: During failover events, attackers may intercept traffic as it reroutes to secondary servers, especially if fallback configurations are not secure.
Assumption 2: CDN Caching Protects Data Integrity
Caching is a core CDN function, storing content closer to users. However, improperly managed caching can introduce risks such as:
- Cache Poisoning: Cyber actors can manipulate CDN caches to deliver malicious or spoofed content to users. For example, injecting a malicious script into cached responses could lead to widespread data compromise.
- Expired Cache Vulnerabilities: Attackers may exploit outdated or improperly invalidated cache entries to serve users old, insecure content that reveals sensitive information.
Assumption 3: TLS/SSL Encryption Secures Traffic
While CDNs enforce encryption through TLS/SSL, weaknesses in implementation or trust models can still be exploited in several ways:
- Man-in-the-Middle (MitM) Attacks: If CDNs rely on outdated or vulnerable certificates, attackers can intercept and decrypt secure traffic. In scenarios where users fail to verify certificates, cyber actors can exploit misconfigured HTTPS setups.
- Compromised CDN Certificates: If a CDN’s root or intermediate certificate is compromised, attackers can impersonate the CDN and intercept data from unsuspecting users.
Assumption 4: CDNs Shield Origin Servers
A key benefit of CDNs is reducing direct exposure of origin servers. However, attackers can bypass CDNs by exploiting:
- IP Leakage: Misconfigurations in DNS or CDN settings can reveal the origin server’s IP address, allowing attackers to target it directly with exploits or DDoS attacks.
- Misconfigured Firewall Rules: If origin servers are not properly secured to only accept traffic from CDN IP ranges, attackers can access them directly.
Assumption 5: CDNs Protect Against Credential Theft
CDNs play a role in safeguarding user interactions with web applications. However, cyber actors can exploit weaknesses such as:
- Credential Harvesting via CDN Caches: Insecure caching policies can result in sensitive data, such as login credentials, being stored in and retrieved from cache by unauthorized users.
- Session Hijacking: Attackers may exploit unsecured session management practices through CDN endpoints to hijack user sessions and gain access to personal accounts.
Assumption 6: CDNs Provide Comprehensive Security
CDNs offer tools such as Web Application Firewalls (WAFs) to mitigate threats, but overreliance on these features means they can still be targeted:
- Insufficient WAF Rules: Default WAF configurations may not cover emerging threats, leaving applications vulnerable to sophisticated attacks like SQL injection or cross-site scripting (XSS).
- Blind Spots in CDN Security: Certain attack vectors, such as application logic flaws or zero-day vulnerabilities, may bypass CDN protections and directly compromise backend systems.
Understanding JavaScript Injection via a CDN
A malicious JavaScript injection occurs when attackers alter a legitimate JavaScript file hosted on a CDN. Once injected, this malicious code is distributed to all the websites relying on that CDN to serve the affected file. Users of those websites unknowingly execute the malicious script in their browsers, potentially exposing sensitive information or enabling other types of attacks.
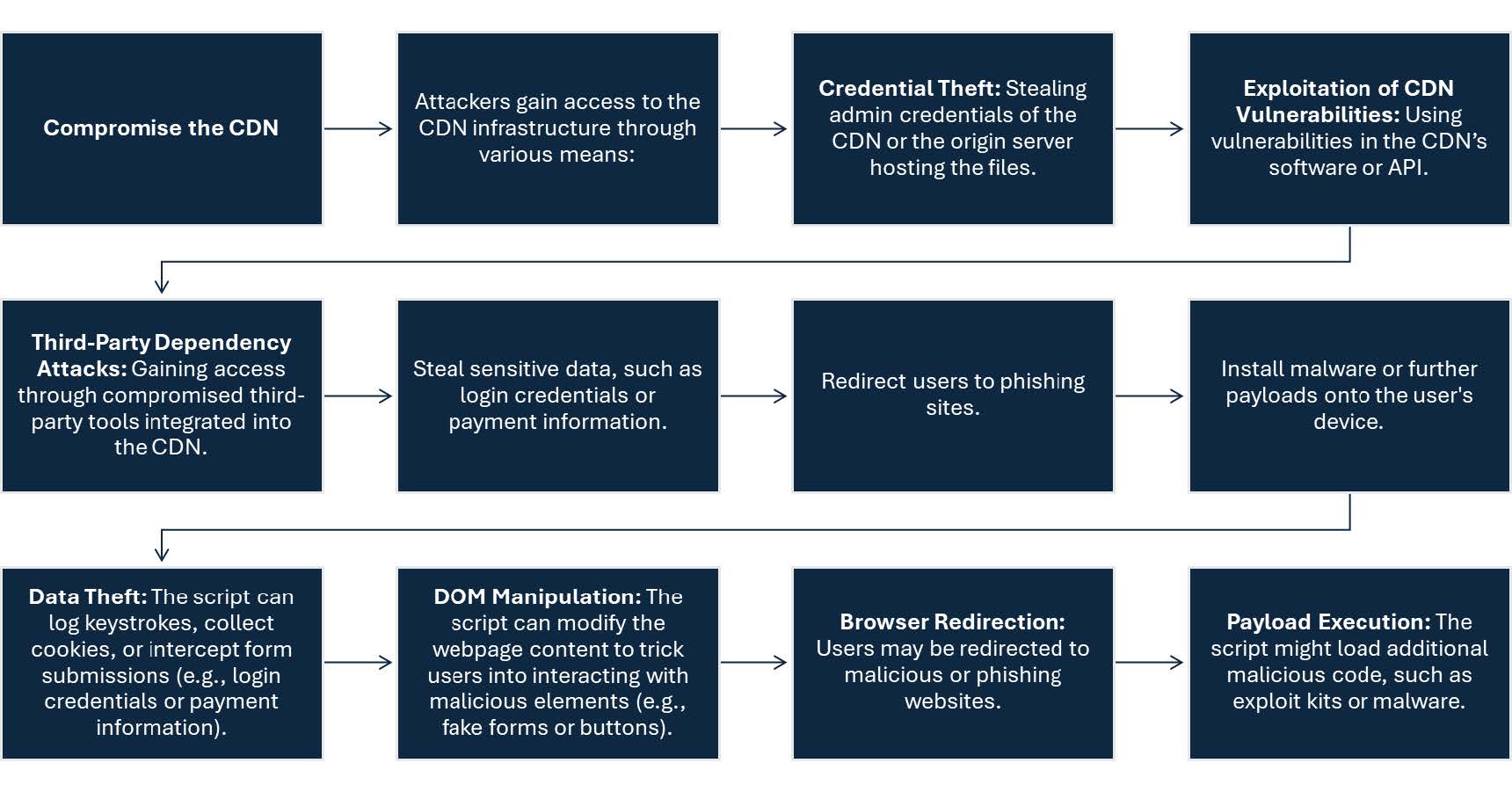
Widespread use of CDNs introduces unique security challenges, as CDNs become attractive targets for threat actors seeking to exploit their role in critical data transmission. To address these risks, a structured and proactive approach to CDN security is critical for ensuring network resilience, safeguarding sensitive information, and mitigating potential vulnerabilities in the digital supply chain. By integrating security principles into every phase of CDN deployment and management, organizations can achieve a balance between performance optimization and operational integrity.
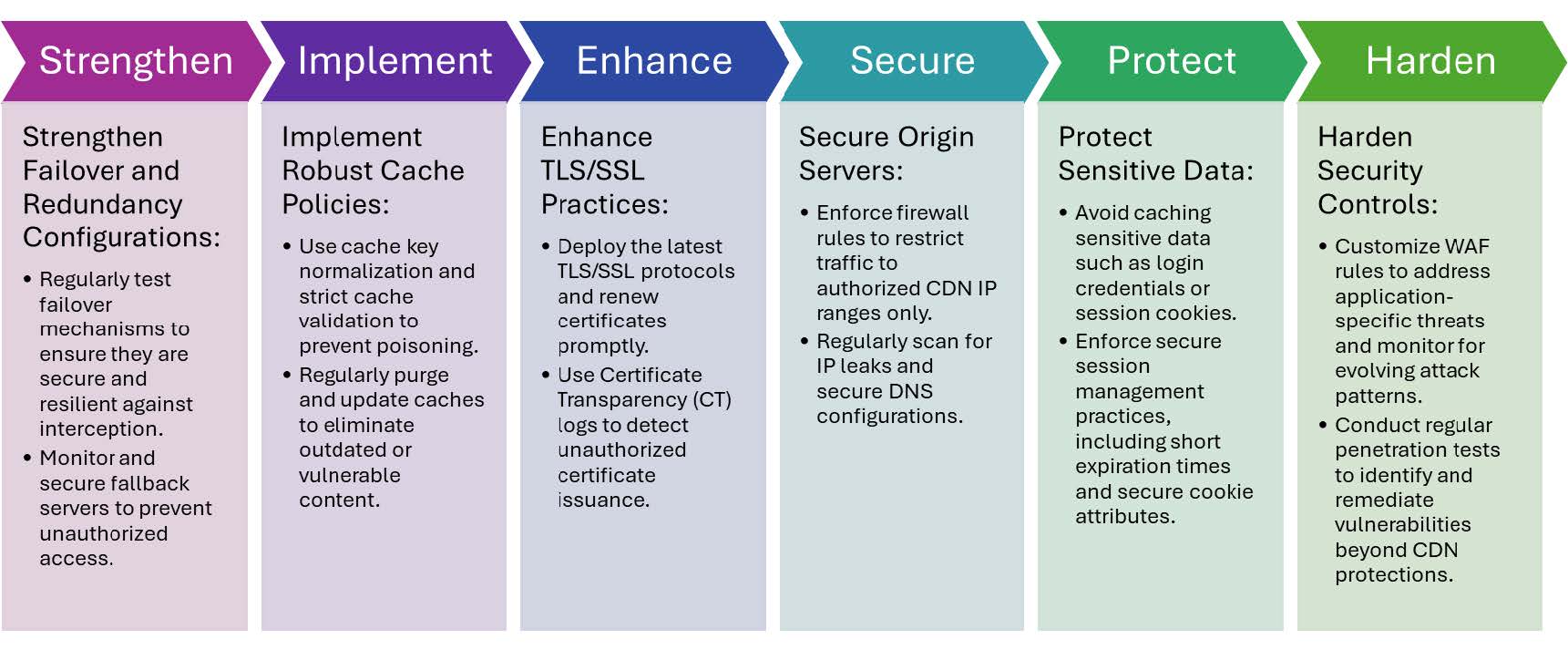
The accompanying chart outlines a strategic process for securing your systems, focusing on key concepts such as access control, encryption, real-time monitoring, and vendor risk assessment. This framework emphasizes the importance of traceability, resilience, and exposure mitigation, in alignment with best practices for digital risk management. By adopting a comprehensive strategy, organizations can identify vulnerabilities, protect against infiltration, and establish a robust response mechanism for mitigating threats to CDN infrastructure. The process not only ensures compliance with security standards but also enhances the overall trustworthiness and scalability of critical online services.
Example: BrowseAloud - A Case Study in Malicious JavaScript Injection via CDNs
In February 2018, over 4,200 websites, including U.S. and UK government domains, were compromised by a JavaScript supply chain attack. The attack targeted BrowseAloud, a widely used assistive technology plugin developed by Texthelp, which provided text-to-speech functionality for accessibility compliance. Attackers compromised BrowseAloud’s JavaScript source code and injected a cryptojacking script designed to covertly mine Monero (XMR), a privacy-focused cryptocurrency, by hijacking visitors’ computing resources.
Attack Execution and Exploited Vulnerabilities
The attack vector exploited third-party script trust—a common weakness in web security where externally hosted scripts are assumed to be secure. Here’s how the compromise unfolded:
- Initial Breach:
- Attackers infiltrated Texthelp’s content delivery infrastructure and injected a malicious JavaScript snippet into the BrowseAloud library.
- The modified script was then automatically loaded by thousands of websites using BrowseAloud, without any visible change to the affected sites.
- Malicious JavaScript Execution:
- The injected code contained a Coinhive miner, a JavaScript-based cryptomining service.
- As users visited infected websites, their CPUs were unknowingly leveraged to mine Monero cryptocurrency for the attackers.
- Since cryptojacking primarily utilizes CPU power, users experienced increased device resource usage, overheating, and performance slowdowns.
- Impact on Government and Public Services:
- U.S. Government Websites Affected:
- U.S. Courts (uscourts.gov) – The official site of the judiciary system, its compromise exposed legal professionals and citizens to cryptojacking.
- Other state and federal websites, including services used for accessibility, tax filings, and healthcare, were also compromised. - UK Government Sites Impacted:
- The Information Commissioner’s Office (ICO) – The UK’s top privacy regulator, responsible for enforcing data protection laws. - The attack remained active for several hours before detection, affecting tens of thousands of visitors.
Detection and Response
Security researcher Scott Helme was among the first to detect the anomaly while running routine scans on public websites. Upon investigating, he found that the affected sites were loading an altered BrowseAloud JavaScript file that contained a Coinhive miner.
Immediate actions were taken to contain the attack:
- Texthelp disabled BrowseAloud within a few hours of detection, preventing further infections.
- Government agencies and website administrators removed the compromised script and conducted forensic analyses.
- Browser security tools and ad blockers updated their signatures to detect and block Coinhive activity.
Lessons Learned & Mitigation Strategies
This incident highlights major security risks in third-party JavaScript dependencies. Several best practices can help prevent similar attacks:
- Subresource Integrity (SRI):
- Websites should implement SRI hash verification, ensuring externally loaded JavaScript has not been tampered with. If the script is altered, the browser blocks execution.
- Content Security Policy (CSP):
- A strict CSP configuration can prevent unauthorized scripts from executing, reducing the risk of injected code running on the client side.
- Zero Trust for Third-Party Scripts:
- Organizations should self-host critical scripts whenever possible, rather than relying on externally controlled resources.
- Continuous Monitoring & Threat Detection:
- Real-time security monitoring of CDN-loaded resources can quickly detect unauthorized changes to hosted files.
- Automated alerts should be configured for unexpected modifications in JavaScript dependencies.
- Regular Security Audits & Code Review:
- Periodic assessments of third-party plugins and dependencies can help identify potential security risks before exploitation occurs.
Why This Attack Matters
The BrowseAloud cryptojacking incident serves as a stark reminder that trusting third-party scripts blindly can introduce systemic vulnerabilities into critical infrastructure, including government websites. Although the attack was financially motivated (mining Monero) rather than destructive, the same method could have been used for data theft, malware delivery, or espionage.
Key Takeaways for Government and Enterprise Security
- Government agencies must implement stricter security policies for third-party dependencies.
- Web developers should prioritize security in content delivery, enforcing SRI, CSP, and code integrity verification.
- Real-time monitoring and rapid incident response can minimize the impact of injected malicious JavaScript.
(Source: https://techcrunch.com/2018/02/12/browsealoud-coinhive-monero-mining-hack/?utm_source=chatgpt.com)
Conclusion
CDNs are essential to modern digital infrastructure, enhancing performance, availability, and security. However, the assumptions of their infallibility introduce critical vulnerabilities that adversaries can exploit. From targeted DDoS attacks on edge nodes and cache poisoning to malicious JavaScript injection and certificate compromises, these risks underscore the need for a proactive, security-first approach to CDN management.
To mitigate these threats, organizations must adopt a multi-layered security strategy that includes Subresource Integrity (SRI), Content Security Policies (CSPs), rigorous access controls, and real-time monitoring. A zero-trust approach should be integrated into CDN deployments, ensuring that every request—regardless of origin—is verified and continuously assessed for anomalies. Additionally, collaboration with CDN providers, periodic security audits, and threat intelligence sharing are essential in building resilience against evolving cyber threats.
Ultimately, CDNs are only as secure as the configurations, policies, and monitoring mechanisms in place. Organizations—especially those handling critical government or enterprise data—must bridge the gap between perceived and actual security, ensuring that CDN infrastructure remains a trustworthy, scalable, and resilient component of their digital supply chain. The future of web security depends not just on leveraging CDNs for performance gains but also on implementing robust safeguards to prevent them from becoming vectors of large-scale compromise.


